Australia’s Best Ransomware Removal Service
Ransomware is a type of malicious software, that stems from cryptovirology that threatens to publish the victim’s data or block access to it, unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts or archives the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
In a properly planned and implemented extortion attack, recovering the files without the decryption key is a difficult problem, but not impossible. But it is even more difficult, is to trace digital currencies used for the ransoms, making tracing and prosecuting the perpetrators. Corporate Data Recovery is here to help.
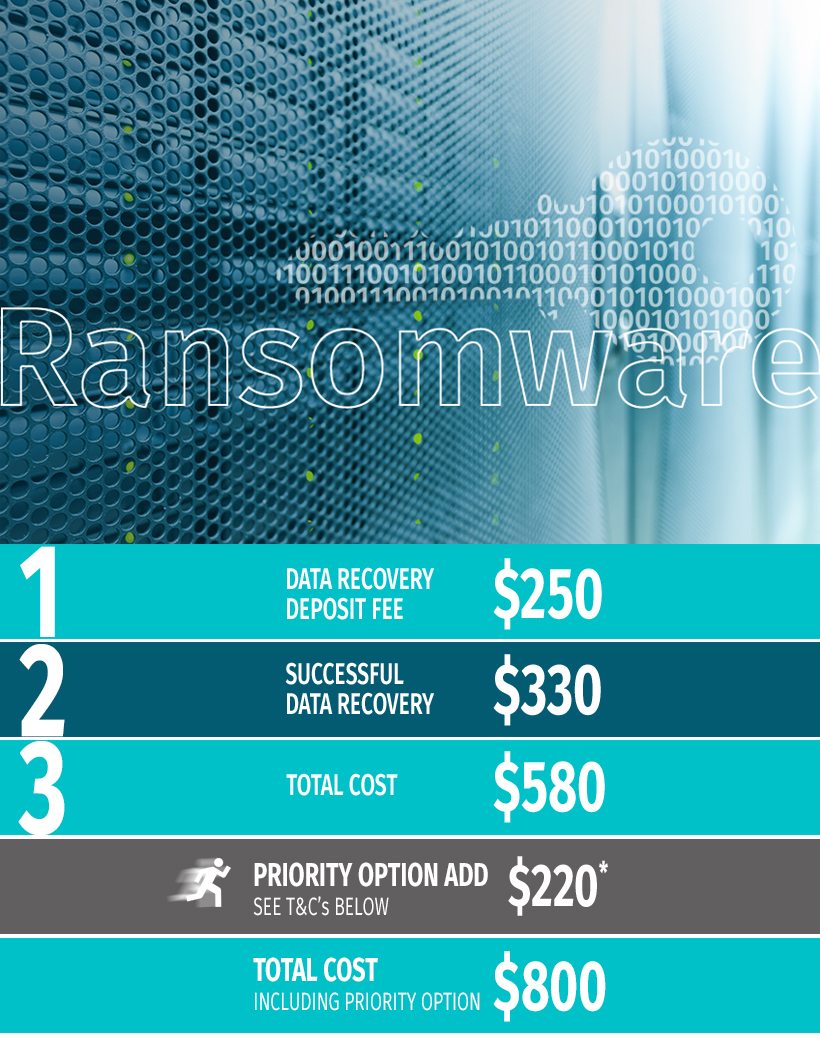
| Step 1. Pay your recovery Assessment Fee | $250 |
| Pay a priority option fee if required | $220 |
| Step 2. Upon successful recovery, pay the successful recovery fee | $330 |
| Your total cost | $580 |
*If your recovery of data requires immediate attention, then click on the Priority Button to select this service. This ensures your drive is placed at the top of the recovery service schedule. Please note, the priority option fee is not included in the total cost above.
Please note: Following the receipt of your hard drive, we will perform extensive testing to recover the data. Whilst we are confident of recovering files that have been blocked from access through a ransomware attack, there are some variations which require specific key codes. In these circumstances you will be informed of the result and options.
Upon successful recovery, your data will be written to a new 1 Terabyte hard drive. If the amount of data recovered is larger than 1 Terabyte, a $110 fee applies per extra Terabytes required.